With organisations and their employees switching to almost exclusively remote working, there have been many unintended consequences to these changing business practices. One example is a significant rise in telecommunications fraud.
What is Telecoms fraud?
Telecoms fraud is the abuse of telecommunications products and services with the intention of stealing money from customers and/or their communications providers. This type of fraud can involve landlines, mobile phones and cloud and on-premise PBX systems.
This sort of fraud, which can also include hacking or theft of service often results in many businesses facing unexpected charges. It’s also becoming increasingly prevalent. According to BICS, over 25 million fraudulent call attempts were made to the UK in 2018, costing millions of pounds. Scammers hack into phone systems to force high call charges from premium rate numbers. These will then usually become payments directly to the hackers.
The good news is that these sorts of activities can be prevented with simple ways of either detecting fraudulent activity or preventing it from happening at all.
Why are we talking about this now?
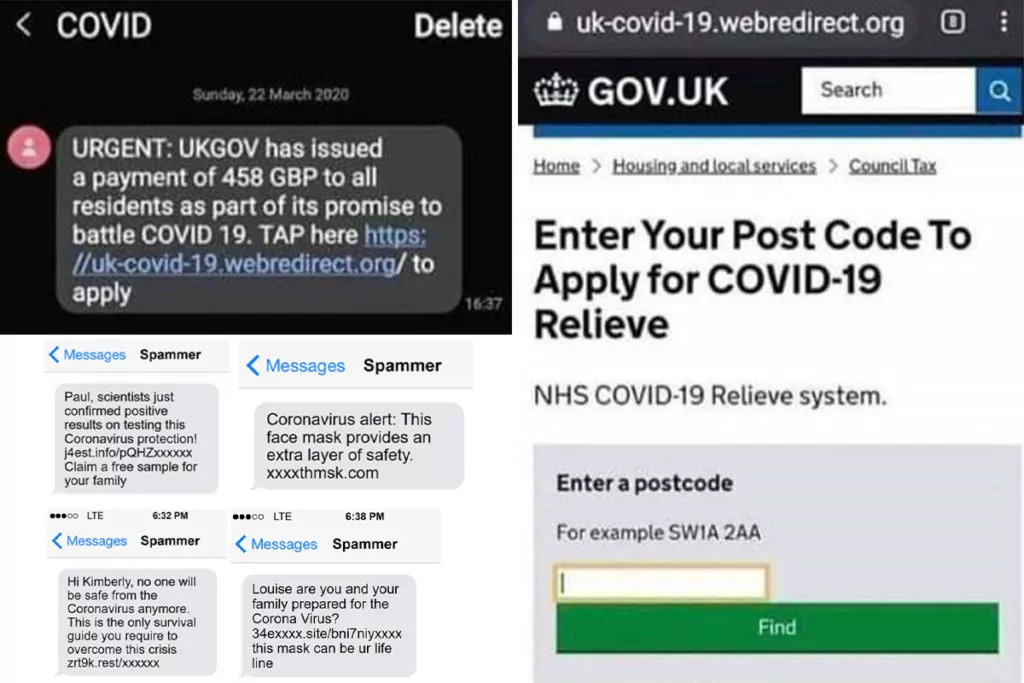
Many scammers are taking advantage of members of the public by using fraudulent calls, emails and text messages. Anxiety around Coronavirus has significantly exacerbated this activity (and responses to it). Scams are aimed at coaxing money and private bank information from concerned people, with many of these messages imitating official organisations including the government, Ofcom and HMRC. It’s also been reported that furloughed or unemployed people are being targeted with messages offering them job roles as key workers.
The UK is the world’s most popular target for phone scams, with 15% of fraudulent traffic directed at British telephone numbers. In research conducted by TechRadar in July 2019, this was said to be because of the regulation of phone numbers. According to TechRadar, the ease at which people can purchase ‘07’ numbers combined with higher mobile termination rates makes it difficult for operators to differentiate between regular phone numbers and scam numbers. So far, £1.6million has been scammed from COVID-19 related fraud and that’s just from Britain alone.
How does Telecoms fraud happen?
There are several ways that fraudulent calls and messages occur. These include providing unrestricted access for making outbound calls, contracting with a fraudulent individual/business or agreeing to standard post payment terms, which provides the scammer with unlimited credit until detected.One key driver of fraud is theft of service. This involves a “hacker” taking control of your business PBX using one of these methods:
Dial-through
Dial-through fraud occurs when hackers access a PBX system through an external port. This allows them to make calls from your PBX system and to route calls through it to high or premium rate numbers. These type of fraud attacks result in you or your business accumulating expensive phone bills and sometimes experiencing crippling financial damage.
A way to avoid this on a conventional PBX system is to restrict the ability for your system to dial certain numbers, such as international or premium rate contacts and specific destinations. We recommend setting up secure PINs and passwords to your phone system, such as voicemail access, extension lines and other features that may be compromised if accessed remotely. A high target area appears to be conference phone units which often get forgotten about with poor usernames and passwords.
If you’re using a VoIP system, ensure that your security measures for both your physical and virtual equipment is safe, strong and secure. This includes firewalls and Session Border Controllers (SBC). It’s also important to regularly monitor your phone system for any changes or increases in call traffic, including reviewing call logging and call reporting where possible.
Need support?
Contact us
Voicemail dial-through
Along the same vain, is voicemail dial-through fraud. This happens when a hacker calls into a voicemail system or mailbox. They enter the voicemail password (usually a default password or an easy-to-guess password combination, like 0000, 1234). This then gives them access to an outside line from which they can make phone calls. Hackers can also break into a voicemail system’s call forwarding feature and make calls. This leads to expensive phone bills and can also jeopardise your business’ reputation. Make sure to regularly update your voicemail passwords to avoid these scams.
Poorly protected SIP Trunks
Another common theft of service is through unprotected or poorly protected SIP Trunks. If SIP Trunks are unprotected or don’t have any security measures in place, like a firewall or DMZ, this leaves the IP ports exposed to being seized or exploited. If this happens, a hacker can use your phone system as their own but avoid the call costs.
You can protect your SIP Trunks by enabling IP authentication. This allows only those within your network to make calls and leave messages. You will also be notified if an unknown source attempts to enter it. You can take simpler steps, like barring certain numbers, setting a maximum default rate for calls and, most importantly, creating strong passwords for your phone system.
Firewall management
A firewall establishes and creates a barrier between an internal network and external network or other untrusted sources and websites. If your firewall has poor management, this means poorly restricted ports and sockets are exposed to viruses and hackers who can get into your trusted network. Make sure your firewall settings and software/patching is up to date and secure to prevent this type of fraud, including locking your ports and sockets.
Password & username management
Weak and lazy usernames and passwords are the most common reason for telecoms fraud or any type of hacking. By choosing simple passwords or ‘easily-guessed’ Usernames and Passwords, this allows hackers to easily get into your accounts or PBX phone system. All businesses and organisations should have a clear and strong policy for PBX password management. This should include password changes or updates on a regular basis and creating complex combinations, using a mix of numbers, letters and other characters/symbols. If you have a lot of passwords for multiple accounts as well as your PBX system, invest in the use of password generation and saving systems, like Passwordstate.

What can you do to avoid Telecoms fraud?
Telecoms fraud and other security breaches can be prevented and minimised by implementing a full end-to-end procedure. Telecoms providers and carriers have fraud alerts in place to alert them of any breaches, like we do at Gradwell. In addition to the measures that we as providers take, it’s important for you to secure your devices and services to strengthen your security and avoid any fraudulent activity or threats.
Due to the unsecure nature of the internet, it’s not always possible to guarantee protection against fraud. However, there are a variety of methods that you can put in place within your phone system’s security that can prevent this further:
Security
The most important action to take when protecting your phone system, PBX or SIP is investing in good security and password/account management software. As we’ve discussed previously, you should be using password generation and saving systems, as well as choosing passwords with complex combinations. It’s also important that you don’t use the same password for multiple accounts or systems. If a hacker finds this password, they can use it to get into and take control of all your systems, so remember to regularly update your passwords and make sure no two passwords are the same.
Another way to protect your systems with passwords is to password protect your handsets. This covers you business line and mobile phone. If you leave your handset unprotected, it’s very easy for a hacker or scammer to get in and set up call features, like forwards and voicemails on the handsets. This solution can be done by both you and your provider.
Calling pattern analysis
Call pattern analysis helps identify patterns in call traffic and monitors and prevents calls which breach or go over specific limits. This can be based around costs, call duration, volume, time of day and call destinations. Call traffic can’t be monitored all the time, however a vast majority of fraudulent traffic can occur during holidays and weekends, when customers and suppliers are away from the office and their devices. Any spikes in traffic should generate automated alerts to relevant parties and this activity can then be restricted, and additional measures can be put into place to protect you and your systems.
Call barring
Call barring lets you bar or block certain types of calls, IP addresses and destinations from being made to or from your phone. Our call barring on our VoIP control panel allows you to block outgoing calls to chosen destinations. You can personalise your call barring settings for both UK and international numbers. It’s also a good idea to bar calls from certain IP addresses and only authorise business or employee IP addresses to make calls.
How our systems protect against fraud
Our systems have built-in security measures and our control panels allow you to further protect your account from fraud and any other breaches. This includes taking steps to protect hardware, changing passwords, create new extensions and daily spending. We have in-depth guides on our support page which covers ways to protect your accounts.
Learn more about our VoIP systems
Talk to us today


